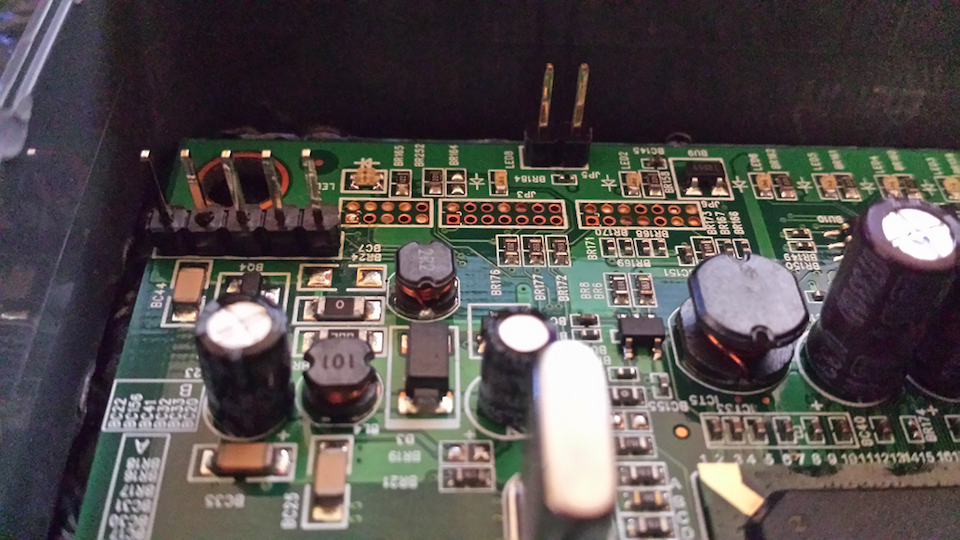
 Gaining console access to the WAG54G home router
Gaining console access to the WAG54G home router
By daniel December 16, 2015
Illustrated guide on identifying and interfacing with the serial pinout exposed on the Linksys WAG54G home router, useful for debugging and exploit dev.
 Why I recommend Chrome to family...
Why I recommend Chrome to family...
By matt September 08, 2015
An analysis of the browser threat landscape and reasoning about browser security for the family user.






