 Cracking the Odd Case of Randomness in Java
Cracking the Odd Case of Randomness in Java
By joseph February 09, 2023
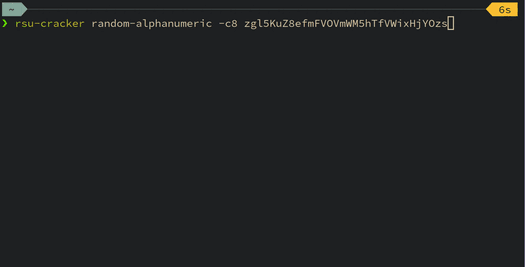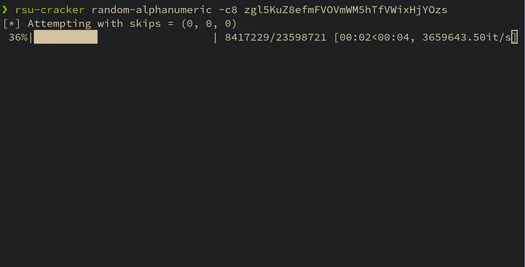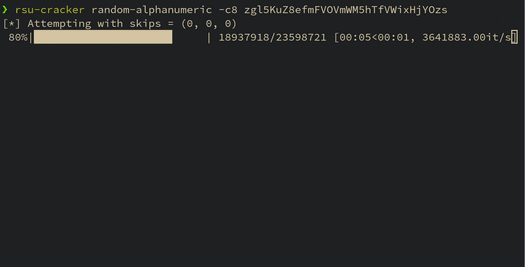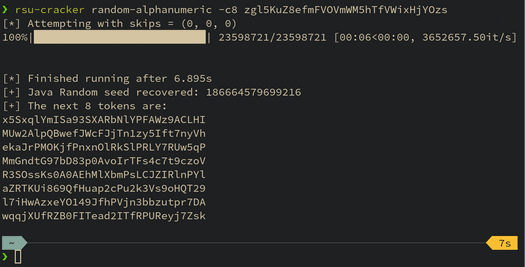
This blog post details a technique for breaking Apache Commons Lang's RandomStringUtils and Java's random.nextInt(bound) when the bound is odd. A tool is released which demonstrates the practicality of the attack.
 Golang code review notes
Golang code review notes
By Zoltan Madarassy June 30, 2022
This blog post is aimed to help people performing security code reviews on Golang code bases to identify dangerous code patterns.
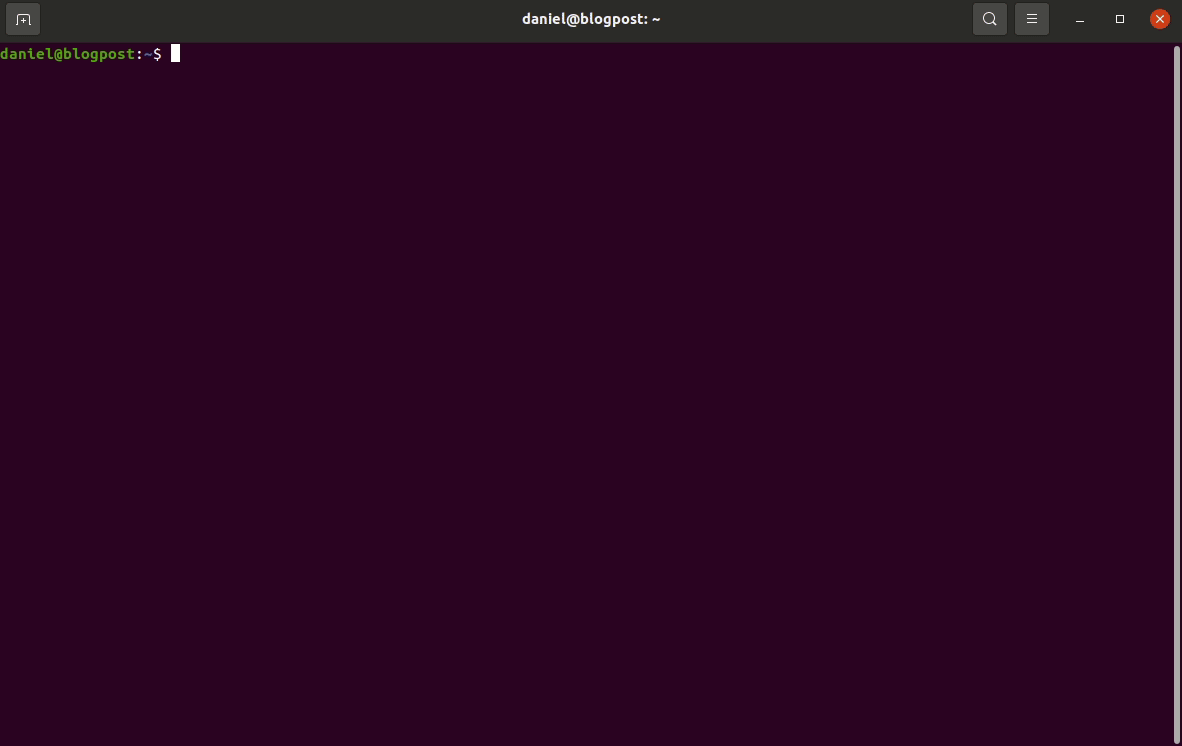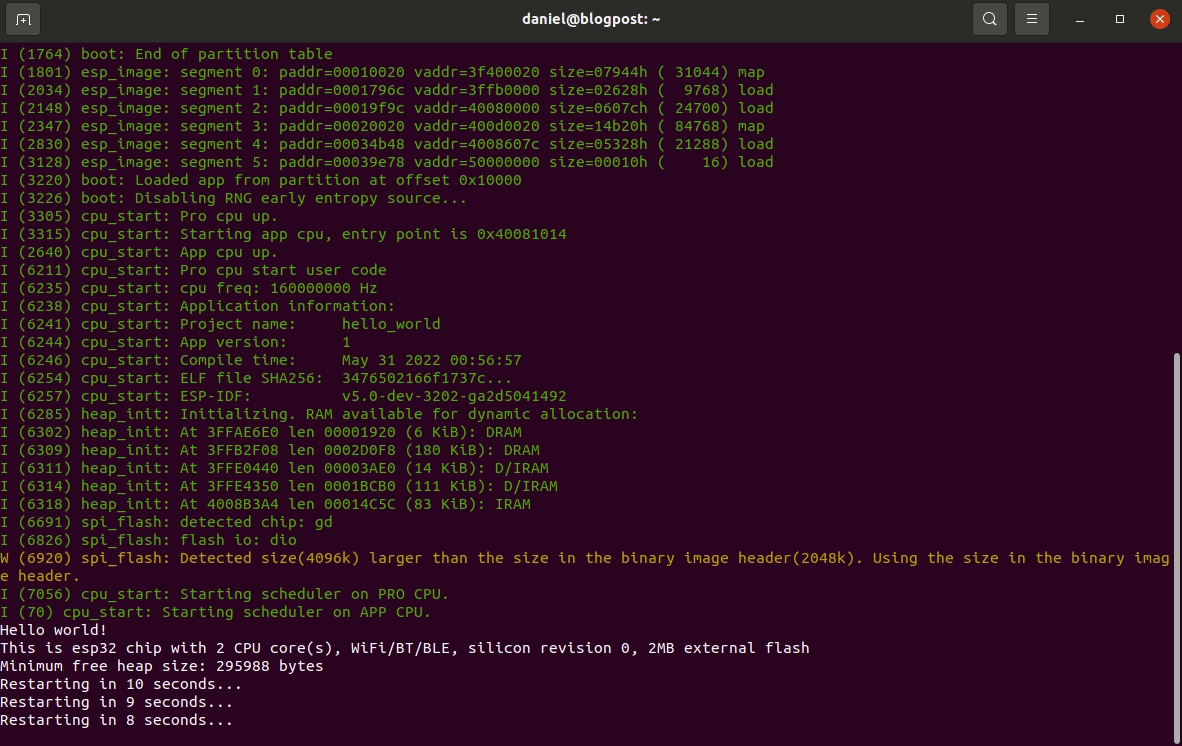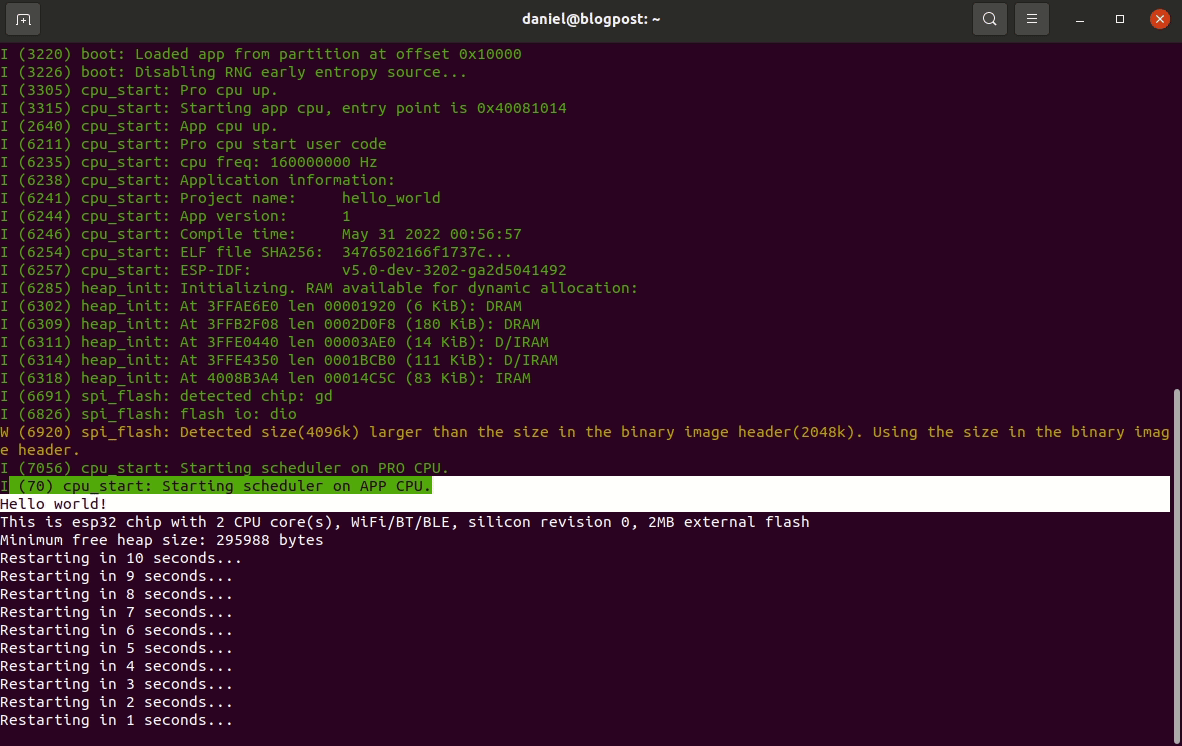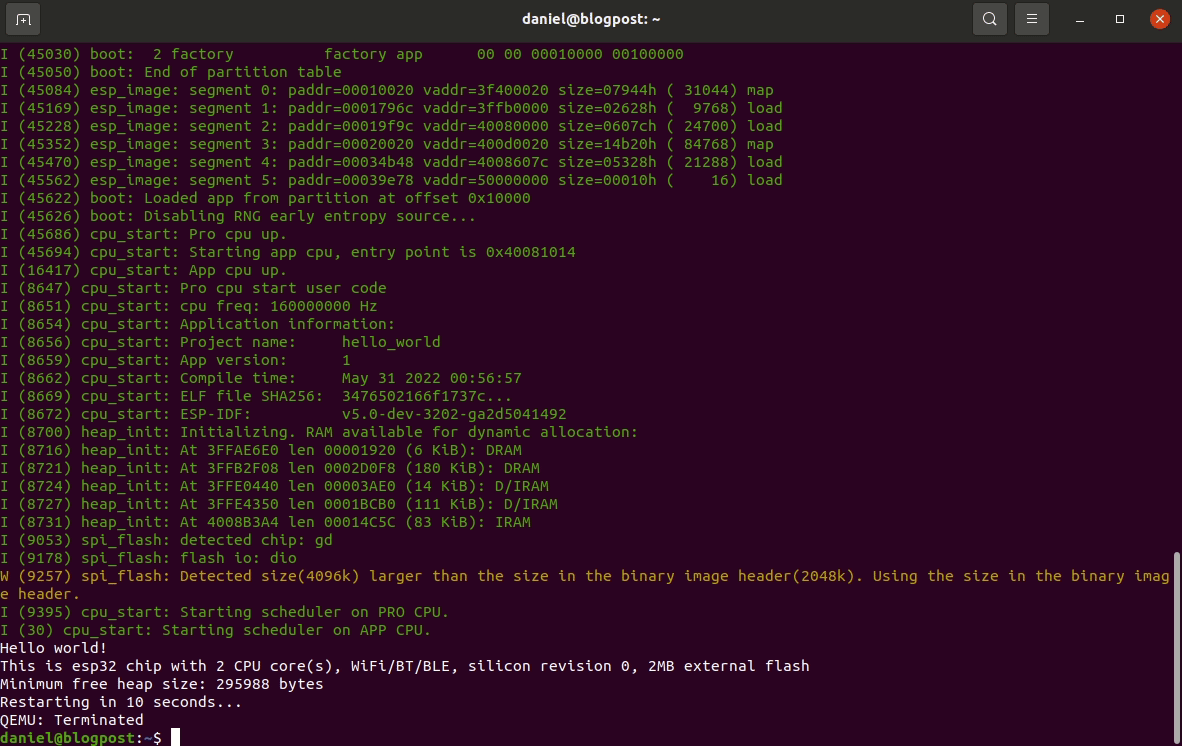 ESP-IDF setup guide
ESP-IDF setup guide
By Daniel Hodson June 06, 2022
This post is for vulnerability researchers looking at the ESP32 and would like a quick setup guide.
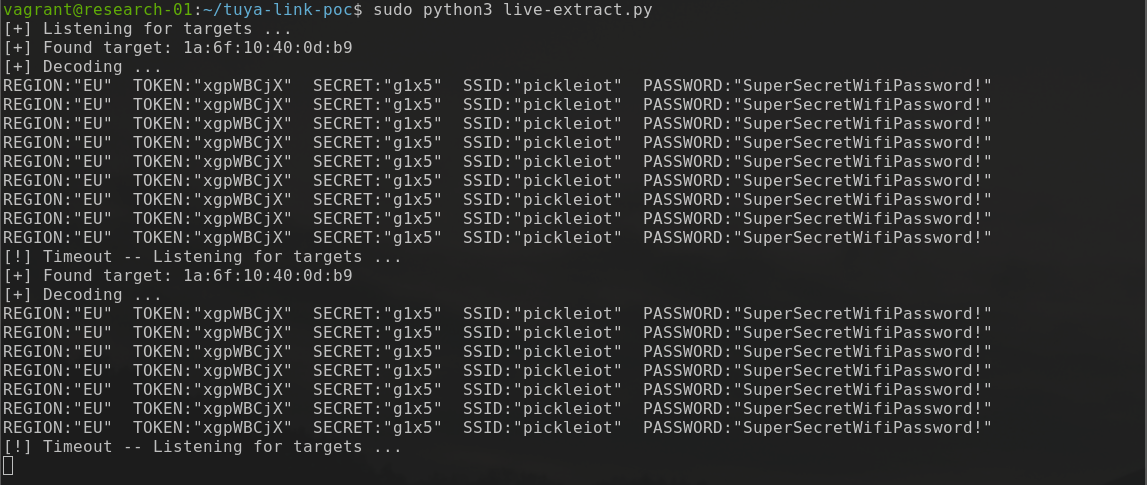 Tuya IoT and EZ Mode Pairing
Tuya IoT and EZ Mode Pairing
By Mykel Pritchard December 09, 2020
This blog post aims to highlight how EZ mode pairing implemented by Mirabella Genio and other Tuya Cloud IoT devices broadcast your WiFi credentials to the neighbourhood.
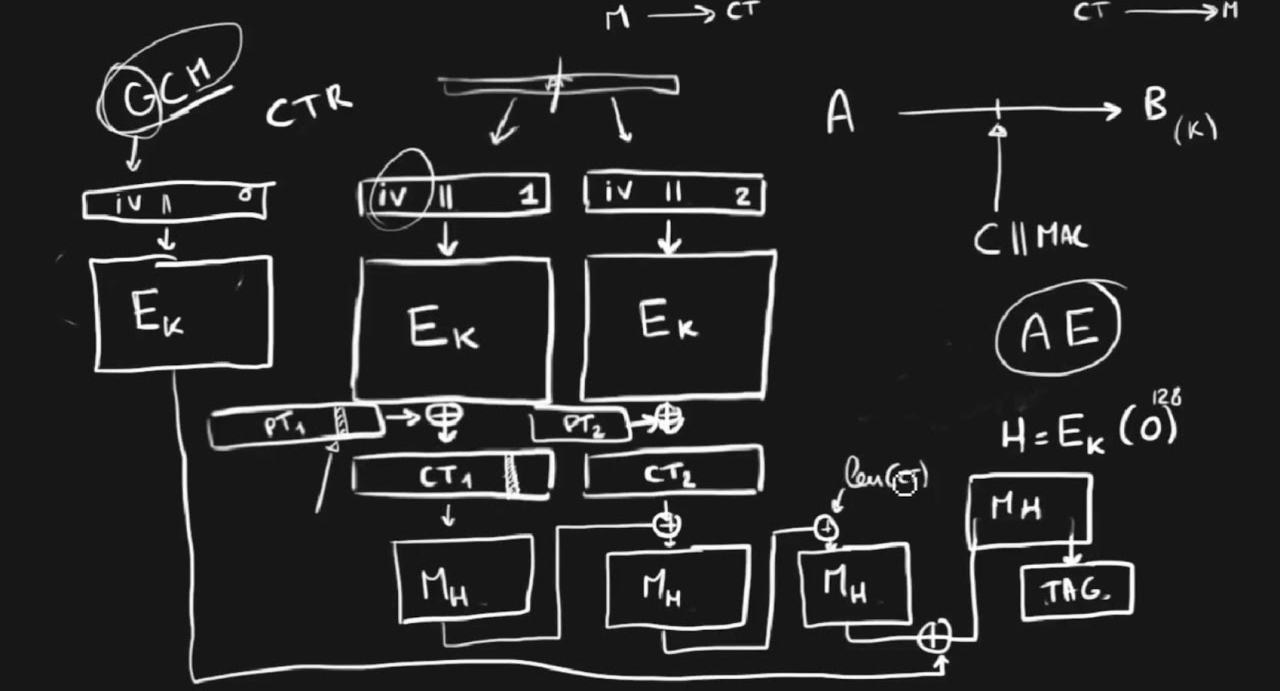 Attacks on GCM with Repeated Nonces
Attacks on GCM with Repeated Nonces
By Sebastien Macke September 25, 2020
This blog post illustrates the security consequences of nonce-reuse in AES-GCM with a Proof of Concept exploit on a vulnerable demo application
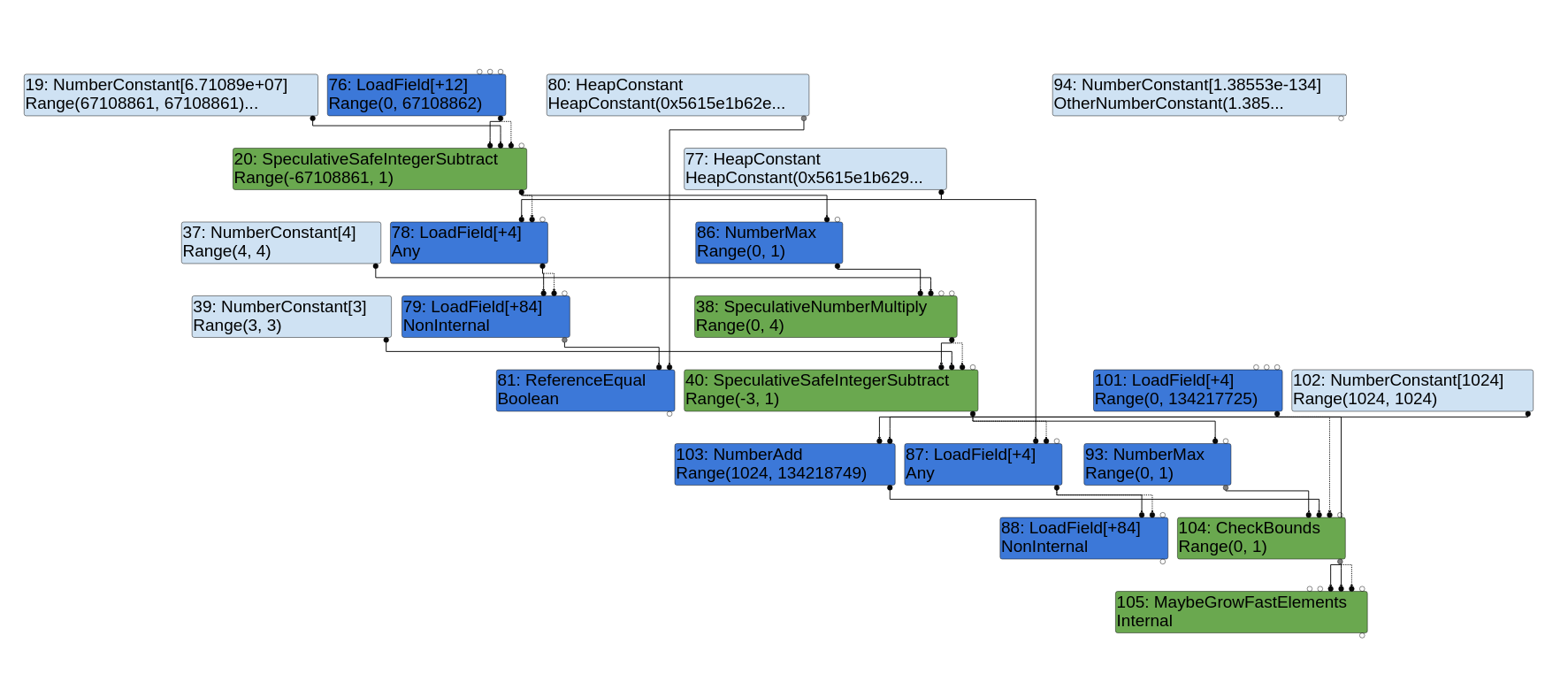 Simple Bugs With Complex Exploits
Simple Bugs With Complex Exploits
By Faraz September 03, 2020
This blog post details a root cause analysis for Project Zero Issue 2046 found by Sergey Glazunov.
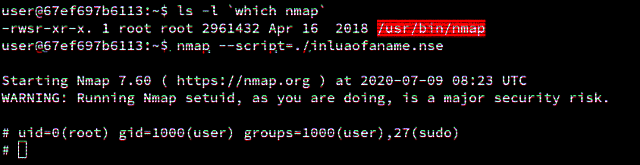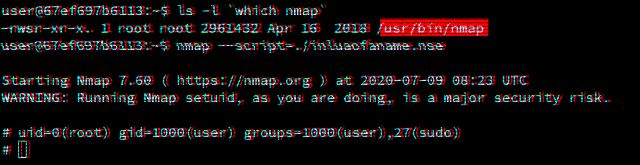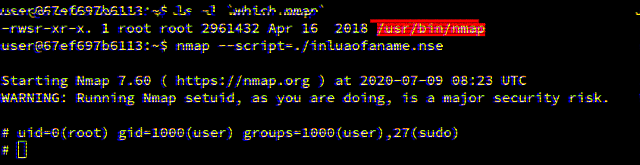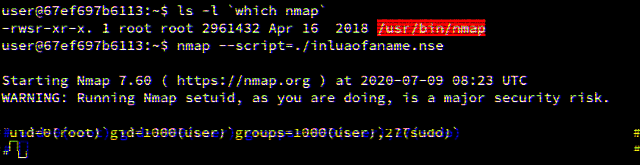 Lua SUID Shells
Lua SUID Shells
By Brendan Scarvell July 09, 2020
This blog post explores how privileged Lua scripts can pop shells without dropping privileges.
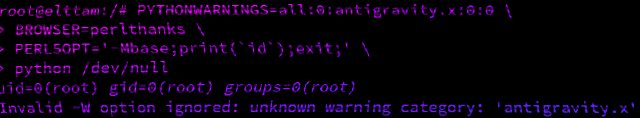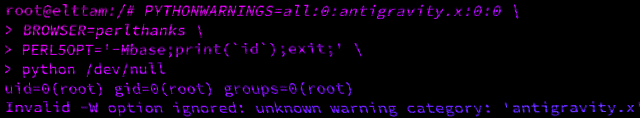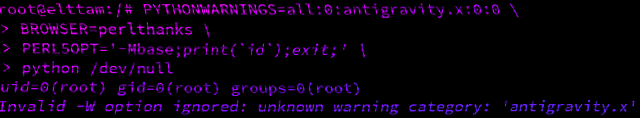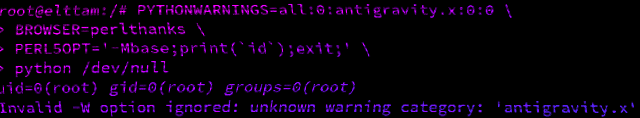 Hacking with Environment Variables
Hacking with Environment Variables
By Luke Jahnke June 24, 2020
A look into how scripting language interpreters can execute arbitrary commands when supplied with malicious environment variables.
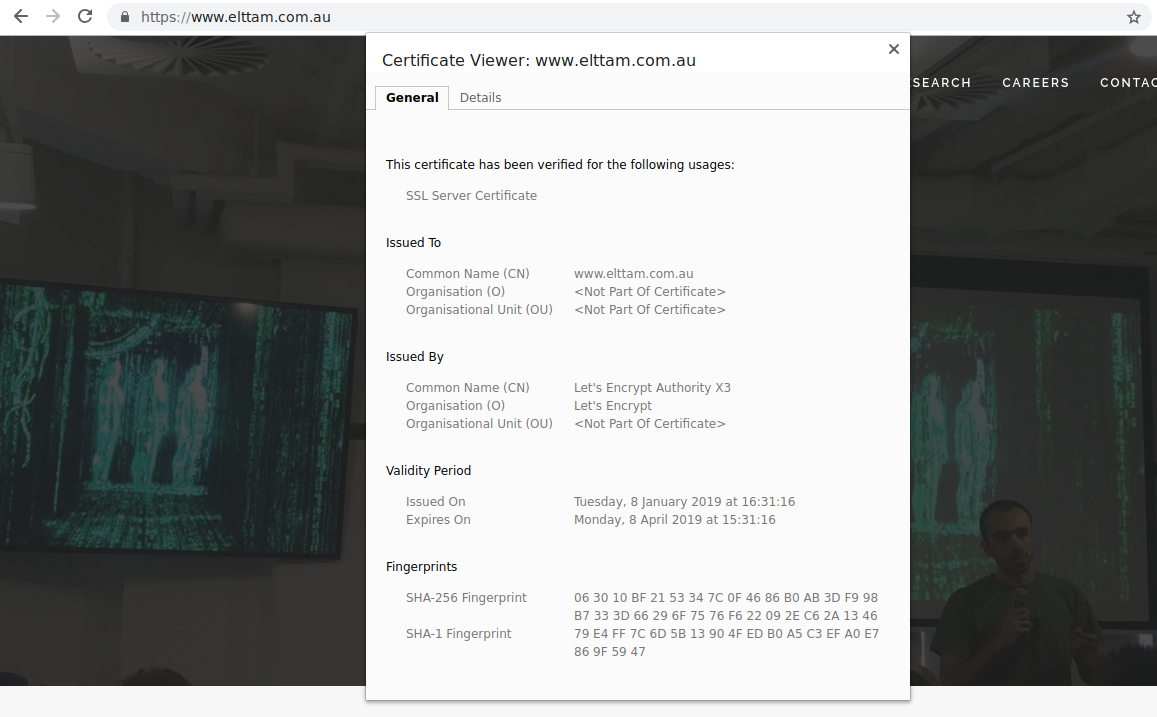 Are you winning if you're pinning?
Are you winning if you're pinning?
By Mykel Pritchard January 24, 2019
This blog post takes a brief look at TLS and certificate pinning, the problem of trust in Certificate Authorities that pinning attempts to address, and discusses whether the lack of certificate pinning in a mobile application constitutes a vulnerability.






